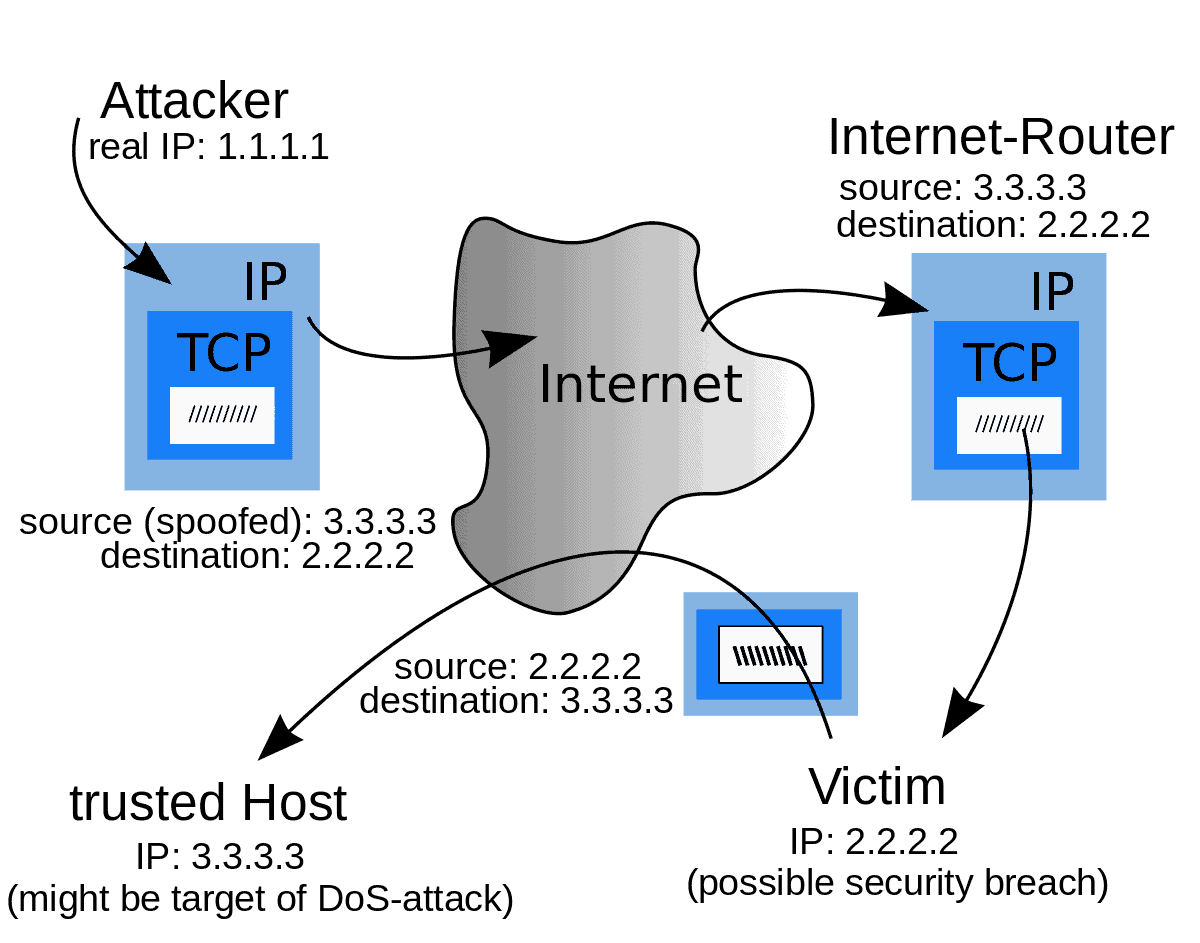
Antispoofing is a technique that prevents traffic with spoofed source IP addresses. Antispoofing prevents cyber-attacks by identifying and dropping packets with a false source address. IP spoofing techniques use spoofed packets, mask the attacker’s identity, launch a reflected DDoS attack, exploit network and system vulnerabilities, and gain unauthorized access to corporate networks and data.
Let us see the simulated IP spoofing attack video:
In a mocking attack, an approaching packet’s source address is changed to appear as though it originated from a known, confided-in source. Mock packets are usually used to complete refusal of administration (DoS) attacks, abuse organization and framework weaknesses, and unapproved admittance to corporate organizations and information.
For instance, if the standard is to sift through heaps with clashing source addresses, a packet that shows a source address from the inward organization will be dropped because outside-confronting interfaces never separate inner bundles.
Antispoofing, which is now and then spelled enemy of mocking, is sometimes executed by Internet Service Providers (ISPs) for the benefit of their clients.
Core Values for Antispoofing Architectures
To be as viable as a conceivable enemy of caricaturing, strategies should be applied near the source as expected under the circumstances. In big business organizations, the head tends to be utilized by each gadget and is frequently controlled and authorized so security reviews can pinpoint precisely which device sent which packet.
For a fruitful execution of MANRS, such fine granularity at the gadget level isn’t vital as MANRS centers around directing security and against satirizing on an organizational level. Subsequently, the standard enemy of mocking structures centers around ensuring clients don’t send packets with unacceptable source addresses.
Which antispoofing technology is used to mitigate DoS attacks?
Antispoofing technology based on implementing switch port security can help mitigate DoS attacks. Switch port security technology allows administrators to limit what addresses are allowed to send traffic on individual switch ports within the switched network.
During a DDoS attack, many connections may be made from the same IP, and limiting connections can help to weed out unwanted traffic. In Cpanel, users can protect themselves from DOS attacks using the ConfigServer Security & Firewall page in the Plugins section of the WHM sidebar menu in the Firewall Configuration section. In addition, users can use the Cpanel IP blocker option to reduce the number of connections from the same IP simultaneously.
- Facebook Ads to Get Followers! - December 27, 2024
- ClickUp vs. Slack - December 20, 2024
- Mastering E-Commerce Analytics: A Blueprint for Success