The Netlogon folder is an essential Windows Active Directory (AD) architecture component. It stores and manages critical information related to the authentication of users, computers, and services in a networked environment. The Netlogon folder provides a secure means of storing credentials and other data associated with user accounts, computer accounts, and domain-specific parameters necessary for adequately functioning a Microsoft Windows domain.
The Netlogon folder is located in the System volume information folder on each domain controller in an Active Directory domain. Several subfolders contain vital information about user logins, computer connections, group policies, certificate templates, system state backups, account lockout policy settings, and more. For example, when a user logs into a network from a workstation or laptop computer by entering their username and password, the authentication request is sent to the Netlogon folder on each Domain Controller for processing. The Domain Controller then verifies that the user has been granted access to the requested resources before sending the credentials back to the workstation or laptop for logon processing.
How Does Active Directory Use the Netlogon Folder?
Active Directory uses the tDirectoryon Folder to store logon scripts. It is a component of Microsoft’s Windows Server operating system and enables administrators to manage user access and permissions to network resources such as computers, servers, printers, and other devices.
Please see the Figure that I created below, which explains how the active Directory uses the directory folder:
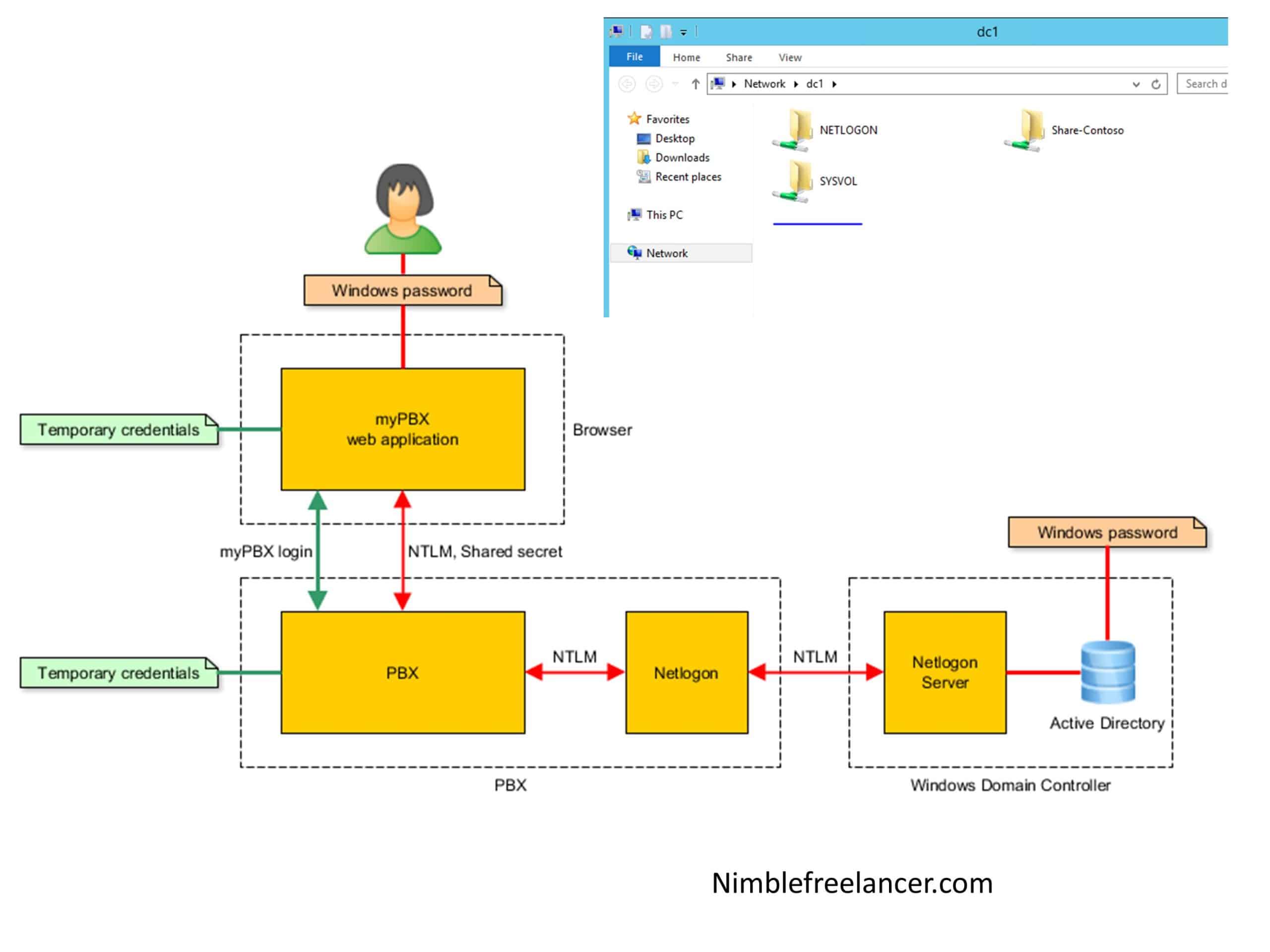
Active Directory stores data as objects, as resources such as printers or computers, or security principals such as users or groups.
Each object on an Active Directory server has its own set of attributes that define it. For instance, a user might have a username, password, and group membership; a printer may have its IP address and model number; and a computer might have its hostname, hardware specifications, and software installed. This rich set of attributes means that administrators can configure their networks according to specific needs.
Active Directory, also known as Directory, allows organizations to structure their networks. Objects are organized into containers, which are further arranged into trees and forests. This will enable administrators to easily control resource access by assigning permissions at each node in the hierarchy based on organizational roles.
The most critical concept when using Active Directory is security principles. Security principles apply across an entire network environment and dictate who can access what type of information or resource. They provide an extra layer of protection against malicious actors, ensuring that only authorized personnel can access sensitive data or systems. This helps organizations maintain compliance with regulatory requirements while safeguarding operations from cyber threats.
In addition to providing security measures and organizing resources in hierarchical structures, Active Directory can be used for authentication when users log onto networks or applications protected by the Windows Server OS. Through integration with Kerberos protocol, users must enter credentials upon logging in so that authorization can be determined accordingly before granting access rights to files, folders, or other resources stored on the server machine(s).
To ensure network reliability and scalability for large organizations, Active Directory supports multiple domain controllers, which act as primary servers for storing user accounts and other information related to user management on the network(s). Additionally, domain controllers communicate with each other over LDAP (Lightweight Directory Access Protocol), allowing them to replicate user accounts across multiple machines without requiring manual input from administrators each time changes need to be made – allowing large-scale organizations with thousands of users spread across different locations around the world manage their networks more efficiently than ever before!
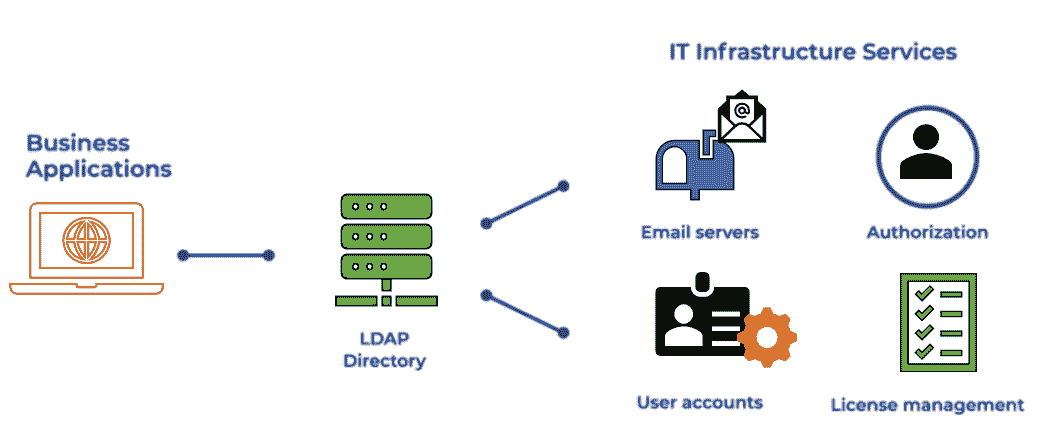
In addition to managing user accounts and authenticating users on a networked environment through its contents within the Netlogon folder, it also stores essential details such as policies related to password management, Group Policy Objects that are used to apply registry-based settings across multiple machines, scripts which can be used to set up automated tasks; backup copies of system files; support files related to Domain Name Services (DNS); files related to security certificates issued by Certificate Authorities; files related to Network Security Service (NSS); dynamic link library (.dll) files used by applications running on client workstations; log files generated during various network events; scripts containing instructions for managing server roles; shared resources such as printers & scanners added through group policies; etc.
The security of data stored within the Netlogon folder is paramount, as any malicious activity within this Directory could Have implications for an entire domain or organization. Hence, administrators should permanently restrict access rights for regular users or services so that only authorized personnel can make changes. Furthermore, since most logins occur via Kerberos version 5 protocol with encrypted ticket authorization process must be carried out at every login attempt hence strong cryptography must be put in place, especially if dealing with sensitive data like bank accounts or similar financial information where encryption keys are exchanged between server & clients while authenticating sessions over networks powered by Windows AD infrastructure.
- Facebook Ads to Get Followers! - December 27, 2024
- ClickUp vs. Slack - December 20, 2024
- Mastering E-Commerce Analytics: A Blueprint for Success